One of the most important Apache modules is the Mod_security, mainly because it enhances your Apache server from cyber attacks. It can effectively block common exploits like code injection attacks using regular expressions and a set of rules that you can modify.
At times, you’d need to disable the Mod_security module. This article explains how to disable the mod_security module correctly without compromising on other modules.
How to Check if Mod_security Module is Available?
Before you think about disabling this module, you need to check if it’s there or not.
When coding the application, developers at times forget to implement the code that prevents attacks.
This is an SQL injection for any website -
If there are no security features, then it will delete the user table in the database. But if there’s Mod_security installed, then it will block the SQL injection.
When there’s the Mod_security module, you’ll see a 406 error. Developers are required to set up the rules for Mod_security to check the http requests made to the server and determine if they’re dangerous.
So to check if Mod_security module is present in the Apache server., then call a string forbidden by the module. If you see a 406 error, then the Mod_security module is enabled.
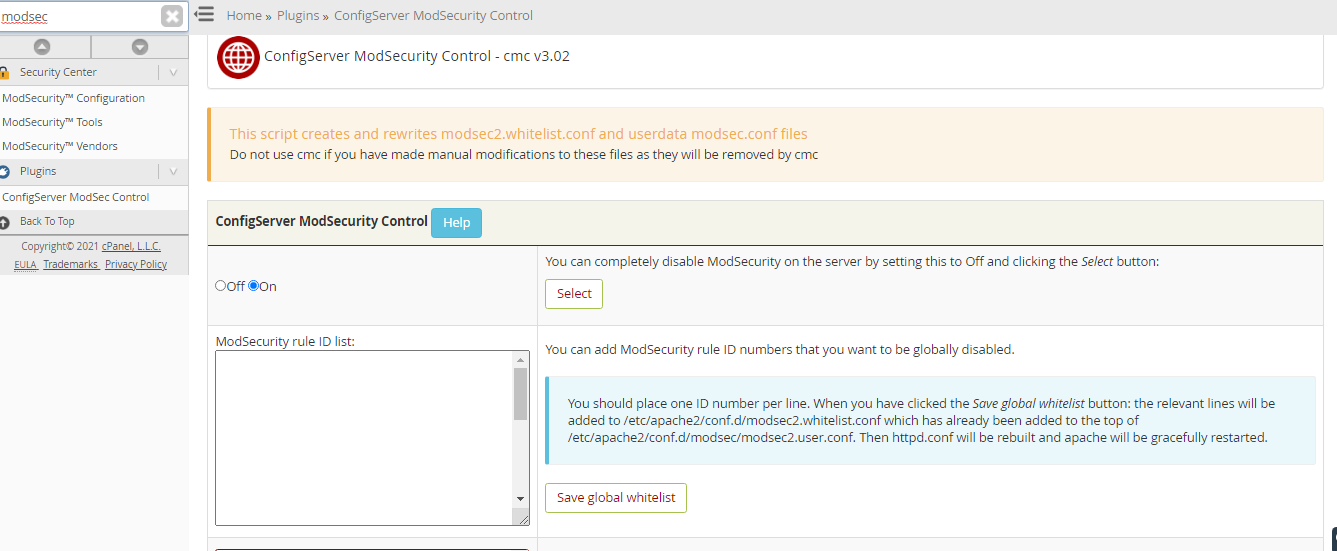
Its very easy to disable modsecurity rule in WHM you can check attached screenshot.
Disable Mod_security Manually on VPS or Dedicated Server
For some applications, it’ll get necessary to disable the Mod_security module so they function correctly. When the need arises, you can disable them at any given time for a particular website.
Here are the steps involved:
This specific line informs Apache to INCLUDE into the VirtualHost config if it finds any file that ends with .conf. It is an advanced concept. So if you’re unfamiliar with it, we suggest you to do some research. Or else, just follow the direction.
Instead of disabling the entire module, you can disable certain rules. If you know which rules to disable, then follow the steps mentioned below:
The SecRuleRemoveById removes any rules with the attributable ID.
It’s also important to not include the SecRuleEngine Off line. Otherwise, it will entirely disable ModSecurity.
If you face any unexpected error, contact your hosting provider.
At times, you’d need to disable the Mod_security module. This article explains how to disable the mod_security module correctly without compromising on other modules.
How to Check if Mod_security Module is Available?
Before you think about disabling this module, you need to check if it’s there or not.
When coding the application, developers at times forget to implement the code that prevents attacks.
This is an SQL injection for any website -
Code:
https://www.webapp.com/login.php?username=admin'”>DROP%20TABLE%20users–.When there’s the Mod_security module, you’ll see a 406 error. Developers are required to set up the rules for Mod_security to check the http requests made to the server and determine if they’re dangerous.
So to check if Mod_security module is present in the Apache server., then call a string forbidden by the module. If you see a 406 error, then the Mod_security module is enabled.
Its very easy to disable modsecurity rule in WHM you can check attached screenshot.
Disable Mod_security Manually on VPS or Dedicated Server
For some applications, it’ll get necessary to disable the Mod_security module so they function correctly. When the need arises, you can disable them at any given time for a particular website.
Here are the steps involved:
- Access your server with SSH and open then httpd.conf file.
- Locate the VirtualHost entry for that particular domain.
- You’re required to uncomment the include link and have it look something like this -
Code:
Include “/usr/local/apache/conf/userdata/std/2/USERNAME/DOMAIN.COM/*.conf”- Next, you need to mkdir the line you just uncommented. Here’s how -
Code:
mkdir -p /usr/local/apache/userdata/std/2/MYUSER/MYDOMAIN.COM- You’re required to insert this rule which would turn off the mod_security module -
Code:
echo “SecRuleEngine Off” > /usr/local/apache/userdata/std/2/USER/DOMAIN.COM/modsec.conf- As a final step, restart your Apache server using “service httpd restart”
Instead of disabling the entire module, you can disable certain rules. If you know which rules to disable, then follow the steps mentioned below:
- grep the domain and look into the Apache error log using this command -
Code:
grep domain.com /usr/local/apache/logs/error_log | grep ModSecurity- You’ll come across a section with the ID field. It should look like this - [id “950003”]
- Then, open the .htaccess file and include this line -
Code:
SecRuleRemoveById 950004It’s also important to not include the SecRuleEngine Off line. Otherwise, it will entirely disable ModSecurity.
If you face any unexpected error, contact your hosting provider.
